Multi-chain has quickly moved from an experimental idea to a default strategic choice for many Web3 founders. Expanding across multiple blockchains promises access to broader liquidity, diversified user bases, and ecosystem resilience. However, as multi-chain adoption accelerates, a critical issue continues to surface: most teams severely underestimate the real multi-chain development cost.
In 2025, building a multi-chain product is no longer just about deploying the same smart contract on several networks. The true cost lies in cross-chain infrastructure, RPC operations, gas abstraction, and security mechanisms that scale non-linearly as complexity increases. This article provides a realistic cost breakdown for 2025, grounded in how multi-chain systems actually behave in production.
What Really Drives Multi-Chain Development Cost in 2025
Most teams misjudge multi-chain development cost for one simple reason: they assume cost scales with deployment, while in reality it scales with coordination and risk. In 2025, multi-chain products should be treated as distributed systems. The cost increase does not come from writing more smart contracts, but from managing how chains interact, stay in sync, and fail safely. The real cost drivers are concentrated in four areas:
- State coordination multiplies, not adds: Each new chain introduces an additional state domain. The system must define how state is synchronized, verified, and reconciled across chains. This coordination logic quickly becomes more expensive than the core contract code itself.
- Cross-chain message paths expand rapidly: Multi-chain communication relies on relayers, proofs, and verification logic. Adding a chain increases the number of message routes, failure cases, and retry mechanisms, all of which require engineering, monitoring, and audit coverage.
- Infrastructure scales unevenly across chains: RPC, indexers, and archival nodes must be provisioned per network. Traffic patterns differ by chain, making infrastructure cost harder to predict and more expensive to operate than in single-chain systems.
- Security surface grows disproportionately: Each chain adds new execution assumptions and new attack vectors. Cross-chain logic cannot rely on single-chain security models, which is why audit scope and re-audit frequency increase sharply in multi-chain environments.
The key insight is that multi-chain development cost grows with the number of interactions and security boundaries, not with the number of deployments.
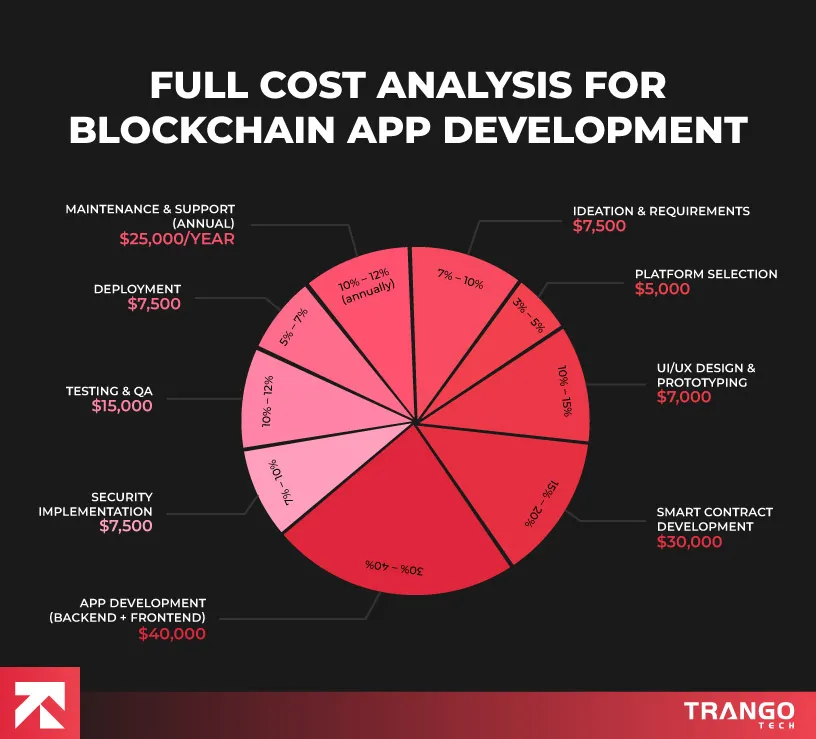
Understanding the True Multi-Chain Development Cost Model in 2025 (source: trangotech)
Teams that treat multi-chain as a deployment checklist typically underestimate cost and face budget overruns later. Teams that design multi-chain architecture around coordination, observability, and security from the start are far better positioned to control cost as complexity increases.
Cross-Chain Infrastructure Cost in 2025
Cross-chain infrastructure is the largest and most underestimated component of multi-chain development cost. Many teams approach this layer as a one-time integration, yet in practice it becomes a long-term source of engineering, operational, and security expenditure.
In 2025, cross-chain infrastructure typically includes bridge logic, messaging and relayer systems, oracle synchronization, and mechanisms for handling partial failures. Whether teams rely on third-party protocols or custom-built components, these elements must be tightly integrated with core smart contract architecture and adapted to the behavior of each supported chain.
Typical cost range (2025): USD 120,000 – 400,000+
The reason this range is so wide lies in how sharply cost escalates based on architectural choices. The main cost drivers can be grouped into four areas:
- Bridge design and integration complexity: Bridge logic is rarely plug-and-play. Even established bridges require careful adaptation to internal contract structures, chain-specific finality rules, and reorganization behavior. Designing safe fallback logic for delayed or failed transfers adds both development and audit overhead, especially as more chains are introduced.
- Messaging and relayer coordination: Cross-chain messaging does not scale with the number of chains alone, but with the number of interaction paths between them. As message volume grows, teams must invest in relayer monitoring, retry logic, and throughput optimization. What begins as an integration task quickly turns into a persistent operational responsibility.
- Oracle synchronization and redundancy: Multi-chain systems rely on consistent data across networks, often requiring multiple oracle providers and verification logic to detect discrepancies. This redundancy improves resilience but increases implementation complexity and ongoing maintenance cost, particularly under volatile network conditions.
- Failure handling across asynchronous environments: Partial failure is the norm in multi-chain systems. One chain may lag while others progress, or messages may arrive out of order. Handling these scenarios safely requires explicit design, testing, and monitoring. Teams that underestimate this layer frequently face costly re-architecture after launch.
A critical mistake is treating cross-chain infrastructure as a build-time expense. In reality, these components must be continuously monitored, upgraded, and coordinated across chains. Each additional network expands the operational surface area, causing costs to compound over time.
The key insight for founders is that cross-chain infrastructure cost grows with coordination and risk, not with feature count. Teams that standardize bridge patterns, limit unnecessary interaction paths, and plan chain expansion deliberately are far more likely to keep this category under control than those that add chains opportunistically.
RPC Cost and Ongoing Infrastructure Expenses
RPC and infrastructure costs are often treated as secondary operational expenses, yet in multi-chain environments they quickly become one of the most persistent and least predictable components of total cost. Unlike core development, these costs do not peak at launch. They scale continuously with usage, cross-chain interactions, and system complexity.
In 2025, RPC and infrastructure cost typically includes RPC provider fees, indexing services, archival nodes, monitoring systems, and redundancy across regions and networks. While these components exist in single-chain systems as well, multi-chain architectures amplify their impact through uneven traffic patterns and read-heavy cross-chain workflows.
Typical annual cost (2025): USD 30,000 – 120,000+
The wide range reflects how infrastructure cost compounds as coordination and reliability requirements increase. The main cost drivers fall into four interconnected areas:
- Per-chain RPC provisioning and redundancy: Each supported chain requires dedicated RPC endpoints, often with failover and regional redundancy. Traffic patterns are rarely uniform across networks, which makes capacity planning more complex and increases the likelihood of overprovisioning to maintain reliability.
- Read amplification from cross-chain logic: Cross-chain systems generate significantly more read operations than single-chain products. State verification, balance checks, and message confirmations across networks amplify RPC usage, particularly under high user activity or automated trading conditions.
- Indexer and archival node requirements: Production-grade applications rely heavily on indexed and historical data. Multi-chain systems must replicate these capabilities across networks, increasing both infrastructure cost and operational complexity. As the number of supported chains grows, so does the burden of maintaining consistent data availability.
- Monitoring and operational overhead: Infrastructure failures in multi-chain systems are rarely isolated. A degraded RPC endpoint on one chain can disrupt cross-chain flows across the entire product. This necessitates more advanced monitoring, alerting, and incident response systems, which add to ongoing operational expense.
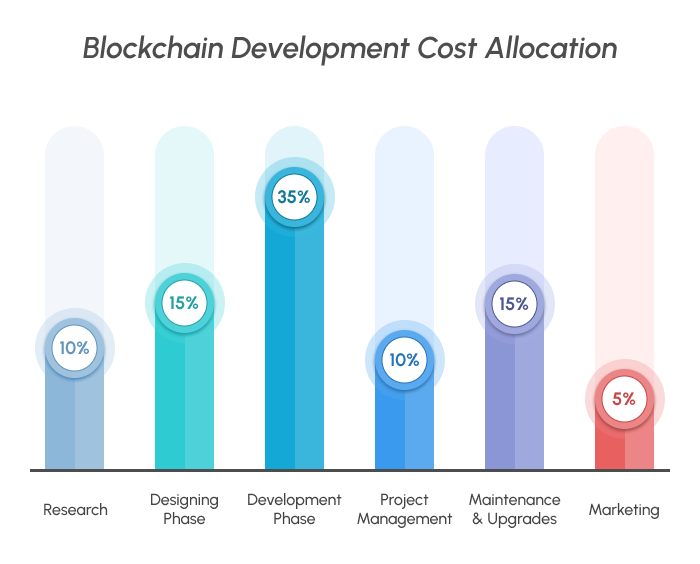
Blockchain development cost allocation showing development, maintenance, and operational overhead (Source: Industry benchmark)
A common planning mistake is to estimate RPC cost based on early-stage traffic or MVP usage. In production environments, RPC usage grows disproportionately as cross-chain interactions, bots, and automated workflows increase. As a result, infrastructure cost often escalates precisely when user adoption accelerates.
The key insight is that RPC and infrastructure cost scales with system activity and reliability expectations, not with feature scope. Teams that consolidate providers, limit unnecessary cross-chain reads, and design for predictable traffic patterns tend to maintain tighter cost control. Those that treat infrastructure as an afterthought often find this category quietly becoming a major contributor to long-term burn.
Security Audit Cost for Multi-Chain Systems
Security audit cost is one of the most misunderstood components of multi-chain development. Many teams assume audit effort scales with the number of smart contracts or lines of code. In multi-chain systems, this assumption no longer holds. Audit scope expands primarily with interaction complexity and attack surface, not with code volume alone.
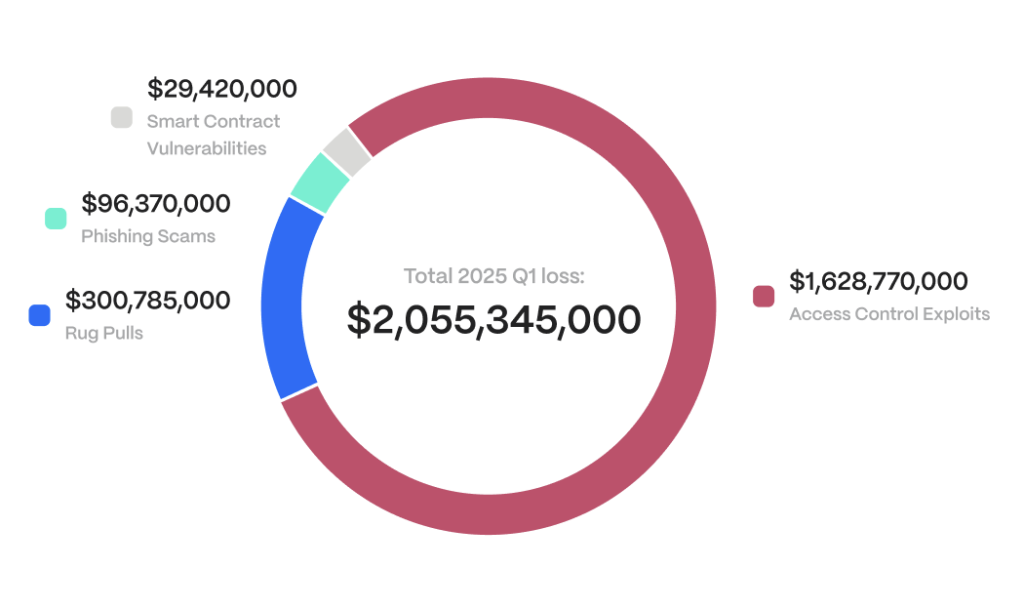
Web3 security losses by exploit type highlighting access control and contract vulnerabilities (Source: Chainalysis)
In 2025, security audits for multi-chain products must cover not only core smart contracts but also cross-chain messaging logic, bridge behavior, relayer assumptions, and failure-handling scenarios. Each supported chain introduces a new execution environment, which significantly increases the scope and depth of security review.
Typical audit cost range (2025): USD 80,000 – 250,000+
The breadth of this range reflects how quickly audit requirements escalate once cross-chain logic is introduced. Several factors consistently drive audit cost upward:
- Cross-chain logic introduces non-linear risk: Cross-chain systems are vulnerable to attack vectors that do not exist in single-chain environments, including replay attacks, message spoofing, delayed execution, and inconsistent state assumptions. Auditors must analyze not only what the system does, but how it behaves when messages arrive late, out of order, or are partially executed.
- Bridge components require dedicated scrutiny: Bridges are among the highest-risk components in Web3. Even when third-party bridge protocols are used, the integration layer must be audited carefully. Custom bridge logic further expands audit scope due to cryptographic verification, validator assumptions, and economic security considerations.
- Audit reusability is limited across chains: While core contract logic may be reused, chain-specific differences in execution, gas behavior, and infrastructure assumptions often require separate validation. As a result, audits cannot simply be “copied” from one chain to another, particularly when cross-chain interactions are involved.
- Re-audits become common as systems evolve: Multi-chain products frequently undergo post-launch changes to optimize performance, adjust infrastructure, or support additional chains. Even small architectural modifications can invalidate previous audit assumptions, triggering partial or full re-audits and increasing total cost.
A critical mistake is treating a security audit as a final milestone before launch. In multi-chain environments, security is an ongoing process that evolves with system complexity. Teams that design cross-chain architecture without standardization often face repeated audits as complexity grows.
The key insight for founders is that security audit cost scales with architectural fragmentation and interaction paths, not with the number of contracts deployed. Teams that standardize cross-chain patterns, minimize unnecessary message flows, and plan audit scope early are far better positioned to contain security spending over the product’s lifecycle.
How Teams Reduce Multi-Chain Development Cost in Practice
Teams that consistently control multi-chain development cost do not rely on aggressive cost cutting. Instead, they reduce unnecessary complexity by making a small number of high-leverage architectural decisions early and revisiting them deliberately as the product evolves. In practice, the most effective approaches fall into four areas:
- Limit and sequence chain deployments deliberately: Rather than launching on multiple networks at once, high-performing teams identify which chains materially contribute to liquidity, user acquisition, or strategic positioning. Each additional chain expands infrastructure, security scope, and operational overhead. Sequencing deployments allows teams to validate demand before incurring full multi-chain complexity.
- Standardize multi-chain architecture from the outset: Cost-efficient teams design reusable contract structures, bridge interfaces, and messaging patterns that behave consistently across networks. This reduces the number of unique interaction paths that must be maintained and audited, lowering both infrastructure cost and long-term security spend.
- Optimize infrastructure footprint for predictability, not just scale
Instead of over-provisioning RPC and indexing services, teams focus on consolidating providers, minimizing unnecessary cross-chain reads, and designing for observable traffic patterns. This approach leads to more stable infrastructure costs as usage grows and avoids sudden budget spikes during periods of increased activity. - Establish security as a repeatable workflow: Treating security as a continuous process rather than a one-time milestone allows audit scope to be reused and extended rather than repeated. Clear separation between core logic, cross-chain components, and infrastructure assumptions significantly reduces the need for costly re-audits as the system evolves.
This is where experienced architectural guidance becomes valuable. Twendee Labs advises Web3 teams on designing multi-chain architectures that reduce infrastructure overhead, optimize the number of deployed chains, and implement clear, scalable security workflows, helping founders avoid the hidden rework that often drives long-term cost overruns.
Conclusion
The most expensive part of building a multi-chain Web3 product in 2025 is rarely what appears in the initial cost estimate. Teams often budget for development, infrastructure, and security in isolation, yet the largest overruns emerge from the gaps between these layers when architectural decisions begin to show their long-term impact.
Hidden costs surface when cross-chain coordination becomes fragile, when infrastructure choices fail to scale predictably, and when security assumptions must be revisited after deployment. Re-architecture, repeated audits, and redeployment across chains are not edge cases. They are common outcomes of treating multi-chain expansion as a deployment exercise rather than a system design problem.
This is why controlling multi-chain development cost is less about negotiating lower implementation fees and more about making disciplined architectural decisions early. Deliberate chain selection, standardized cross-chain patterns, and security-first workflows significantly reduce rework as complexity grows.
This is also where experienced architectural guidance makes a measurable difference. Twendee Labs works with Web3 teams to design multi-chain architectures that prioritize cost control, security clarity, and long-term operability, helping founders avoid the hidden rework that quietly inflates budgets as products scale.
In 2025, the question is no longer whether a product can be multi-chain, but whether it is architected to remain sustainable once it is.
Contact us: Twitter & LinkedIn Page
Read latest blog: Why Web3 Apps Need Risk Oracles, Not Just Price Oracles





